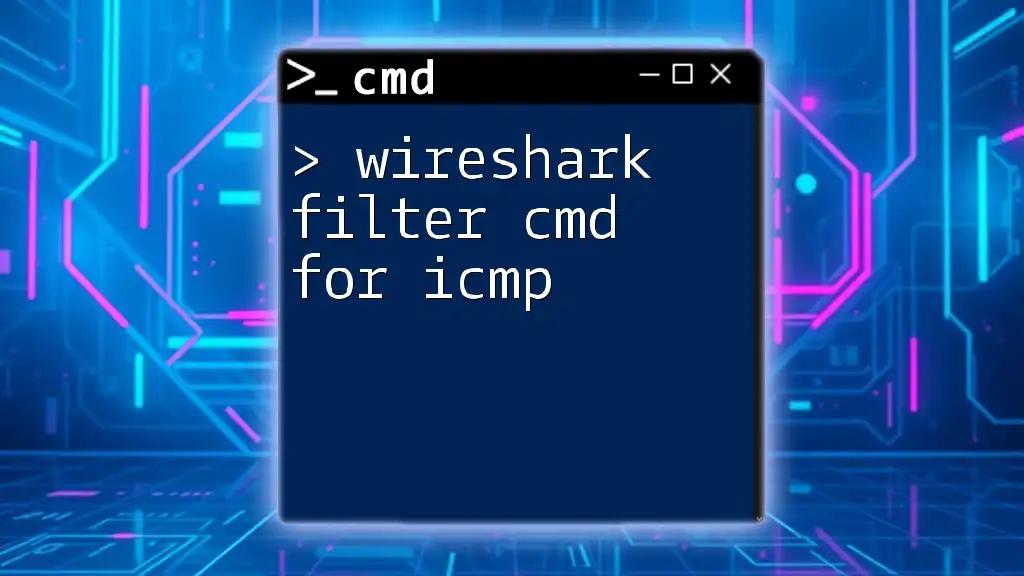
Wireshark can filter ICMP packets using the display filter command `icmp`, allowing users to analyze network traffic related to the Internet Control Message Protocol.
Here’s the command in markdown format:
icmp
Setting Up Wireshark for ICMP Analysis
Before diving into the practical application of Wireshark filter cmd for ICMP, it is essential to have Wireshark installed and to know how to capture ICMP traffic effectively.
Installing Wireshark
To get started, you need to install Wireshark on your system. Here are the steps to follow:
- Visit the [Wireshark download page](https://www.wireshark.org/download.html).
- Choose the appropriate version for your operating system (Windows, macOS, or Linux).
- Follow the installation prompts, ensuring that you include any necessary dependencies, such as WinPcap or Npcap for Windows users.
Once installed, launch Wireshark, and you will be greeted by the main interface.
Capturing ICMP Traffic
Capturing ICMP packets is crucial for effective network analysis. You can begin a capture session by following these steps:
- Selecting the Correct Network Interface: Choose the network interface that corresponds to your active connection (e.g., Wi-Fi, Ethernet).
- Starting a Capture Session: Click on the interface to start capturing packets. You will see a stream of captured data flowing into the main window.

Understanding Filters in Wireshark
Overview of Display Filters
Filters are a powerful feature in Wireshark, allowing users to focus on specific traffic for analysis. Display filters control what packets are shown in the packet list, making them essential for efficient analysis.
Difference Between Capture and Display Filters
It's vital to distinguish between capture filters and display filters.
- Capture Filters: Applied while capturing network traffic. They limit the packets captured to only those matching specified criteria.
- Display Filters: Applied to the packets post-capture. They refine the packets displayed based on specific conditions.
Understanding this difference helps in optimizing your analysis workflow.

Using Wireshark Filters to Isolate ICMP Packets
Basic ICMP Filter Command Syntax
To analyze ICMP traffic effectively, you must utilize the correct filter commands. The most straightforward command to filter for ICMP packets is simply:
icmp
This filter shows all ICMP packets in your capture.
Advanced Filtering Techniques
Filtering for Specific ICMP Types
Wireshark allows you to dig deeper and filter for specific ICMP message types. For example, if you want to isolate Echo Requests (commonly known as pings), you can use:
icmp.type == 8
Conversely, to filter for Echo Replies, the command is:
icmp.type == 0
Combining Filters
Sometimes, you may want to view multiple types of ICMP traffic simultaneously. To do this, you can combine filters. For instance, to see both Echo Requests and Echo Replies, you would use:
icmp.type == 8 or icmp.type == 0
This command grants visibility into both request and response interactions between systems, helping you observe the exchange outcomes.
Practical Applications of ICMP Filters
Diagnosing Network Issues
ICMP is invaluable for troubleshooting network connectivity. By applying the wireshark filter cmd for icmp, you can pinpoint issues related to packet loss, latency, or connection failures. For instance, if you see a consistent stream of Echo Replies with high latency, this could indicate network congestion.
Monitoring Network Performance
Using ICMP filters, you can measure round-trip time (RTT) between devices. When filtering for Echo Requests, you can assess how long it takes for responses to return. This information is crucial when determining the efficiency of a network connection.
Security Implications
Monitoring ICMP traffic also has security benefits. Unusual ICMP patterns could indicate network scanning or unauthorized attempts to communicate with devices. Regularly filtering and analyzing ICMP packets can help identify potential security threats before they escalate.
Common Mistakes When Using Wireshark ICMP Filters
Misunderstanding ICMP Types
One common mistake is confusion regarding the various ICMP message types. A comprehensive understanding of these types is vital to making accurate assessments and troubleshooting effectively. Familiarize yourself with less common ICMP messages, like Destination Unreachable and Time Exceeded, which can provide critical diagnostic insights.
Filter Syntax Errors
Syntax errors in filter commands are another frequent pitfall. Pay close attention to the structure of your commands. For example, always remember to use double `==` when specifying types and to keep logical operators, such as `or`, correctly formatted.
Conclusion
The ability to filter packets effectively in Wireshark, particularly for ICMP, unlocks a realm of insights into network performance and troubleshooting capabilities. By mastering the wireshark filter cmd for icmp, you gain the tools necessary for both diagnosing issues and optimizing network operations.
Continually practicing these commands will enhance your skills and equip you with the confidence to tackle network analysis challenges head-on. With the basics in hand, take your first steps toward becoming a proficient user of Wireshark filters and discover the hidden stories embedded within your network traffic.
Additional Resources
For further reading and practical applications, consider diving into the official Wireshark documentation and tutorials. They offer in-depth insights into the functionality and capabilities of Wireshark, helping you expand your knowledge and expertise in network analysis.